
by Anil Jalela | Oct 21, 2022 | DevOps
Jenkins:-
→ Jenkins is an Open-Source project Written in Java that runs on Windows, macOS, and Other Unix-like Operating Systems. It is free, Community Supported, and might be your first-choice tool for CI.
→ Jenkins automates the entire Software development life Cycle
→ Jenkins was Originally developed by Sun Microsystem in 2004 under the name Hudson.
→ The project was later named Jenkins when Oracle bought Microsystems.
→ It Can run on any major platform without any Compatibilities issues.
→ Whenever developers Write Code, we integrate all that Code of all developers at that point in time and we build, test, and deliver/Deploy to the client. This process is called CI/CD ..
→ Jenkins helps us to achieve fast development.
→ Because of CI, Now bugs will be reported fast and get rectified fast So the entire Software development happens fast.
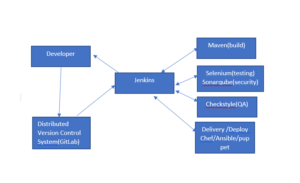
Workflow of Jenkins:-
→ We Can attach git, Maven, Selenium, Sonarqube, and Artifactory plugins to Jenkins.
→ Once developers put Code in GitHub, – Jenkins pulls that Code & sends to Maven for build
→ Once the build is done Jenkins pulls that Code and sends it to Selenium for testing.
→ Once testing is done, then Jenkins will pull that Code and Send it to artifactory (archive) as per requirement and so on.
→ We Can also deploy codes with Jenkins.
Build means=( compile, code review, unit testing, Integration testing, packaging[tar,jar,exe] )
Advantages of Jenkins: –
→ It has lots of plug-ins available
→ You Can Write your own plug-in.
→ You Can use Community Plug-in.
→ Jenkins is not just a tool. It is a framework i.e.: – You Can do whatever you want All you need is plug-ins.
→ We Can attach Slaves (nodes) to Jenkins master. It instructs others (slaves) to do Job. If slaves are not available Jenkins itself does the job.
→ Jenkins also behaves as a crone Server Replacement. i.e.: – Can do the scheduled task.
→ It Can Create Labels
| 1 |
yum install yum install fontconfig java-11-openjdk.x86_64 |
install java |
| 2 |
alternatives –config java |
the set version of java |
| 3 |
cp /etc/profile /etc/profile_backup |
backup profile |
| 4 |
echo ‘export JAVA_HOME=/usr/lib/jvm/ /usr/lib/jvm/jre_11_openjdk’ |tee -a /etc/profile |
export java development kit home |
| 5 |
echo ‘export JRE_HOME=/usr/lib/jvm/jre’ | tee -a /etc/profile |
export JVM home |
| 6 |
source /etc/profile |
export configurations in the current system environment |
| 7 |
wget -O /etc/yum.repos.d/jenkins.repo https://pkg.jenkins.io/redhat-stable/jenkins.repo |
Download the stable repo for yum |
| 8 |
rpm –import https://pkg.jenkins.io/redhat-stable/jenkins.io.key |
Import key for package signature verification |
| 9 |
yum install jenkins |
Install Jenkins |
| 10 |
systemctl start jenkins.service |
Start Jenkins service |
| 11 |
systemctl enable jenkins.service |
Enable Jenkins service |
what needs to learn in Jenkins?
Introduction to Jenkins
Introduction to Continuous Integration
Continuous Integration vs Continuous Delivery
Jenkins Overview
Characteristics and features
Architecture
Concepts and Terms
Benefits and Limitations
Installation and Configuration
Jenkins Installation and Configuration
Plug-ins Overview
Integration with Git
Integration with Maven
Integration with Java
Installing plugins
Setting up Build Jobs
Jenkins Dashboard
Create the first job
Running the first job
Manage jobs – failing, disable, update and delete
Pipeline with Jenkinsfile
Freestyle Project Configuration
Git Hooks and Other Build Triggers
Workspace Environment Variables
Parameterized Projects
UpstreamDownstream Projects and the Parameterized Trigger Plugin
Build a Java application with Maven using Jenkins
Continuous Delivery Pipeline
Publishing Build Artifacts
Deployment Plug-in setup and configuration
Auto Deployment of build artifacts into the target server
Deploy a Java application with Maven using Jenkins
Executing selenium Functional Testing with deployment
Management, Security and Best Practices
Managing and Monitoring Jenkins Server
Scaling Jenkins
Securing Jenkins
Adding Linux Node and executing job on it
Adding windows node and executing job on it
Configuring access control on Jenkins
Configuring role-based access control
Jenkins logs
Management
Credentials in Jenkins
Best Practices
Jenkins Pipeline
Writing Jenkins Pipeline file for java application build and deployment
Storing Jenkins in git and configuring webhook
Difference between declarative and scripted pipeline
Specify an agent in the pipeline
Parameters in Pipeline
Schedule build in the pipeline
Webhook in pipeline
Approval in pipeline
Approval with timeout in the pipeline
Variables in pipeline
Email notification in the pipeline
Post-build action in the pipeline
Parallel stages in the pipeline
Condition in pipeline
Selenium Functional Testing in the pipeline

by Anil Jalela | Oct 20, 2022 | Linux
Yum (Yellowdog Update Modified) is an RPM Packet Management system for Fedora, CentOS, Red Hat, OpenSuse, etc. Yum, history (list, info, summary, repeat, redo, undo, new) commands is added on the 3.2.25 version. So this works for every Linux Distros, which uses yum 3.2.25 or newer. Yum, history command is really useful in situations where the need to example roll back the latest yum activity or undelete some deletes or just see what is updated lately.
Yum history and Yum history list
yum history lists all the latest yum operations and yum history list all operations or just selected package operations
Listing all operations
[root ~]> yum history
### OR ###
[root ~]> yum history list
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
ID | Login user | Date and time | Action(s) | Altered
————————————————————–
45 | System <unset> | 2010-01-18 09:57 | I, U | 21
44 | User <username> | 2010-01-14 15:31 | Install | 1
43 | System <unset> | 2010-01-14 08:13 | Update | 19
42 | System <unset> | 2010-01-13 10:39 | I, U | 40
41 | System <unset> | 2010-01-11 07:59 | Update | 16
40 | System <unset> | 2010-01-08 07:58 | Update | 38
39 | System <unset> | 2010-01-07 08:39 | I, O, U | 39
38 | System <unset> | 2010-01-05 08:23 | O, U | 18
37 | User <username> | 2010-01-04 15:43 | Install | 1
36 | System <unset> | 2010-01-04 07:56 | Update | 66
35 | User <username> | 2009-12-30 10:07 | Install | 2
34 | User <username> | 2009-12-30 10:01 | Update | 15
33 | User <username> | 2009-12-30 08:14 | Install | 13
32 | System <unset> | 2009-12-29 07:52 | I, U | 26
31 | System <unset> | 2009-12-28 08:31 | E, I, U | 66
30 | System <unset> | 2009-12-23 12:11 | Update | 7
29 | System <unset> | 2009-12-22 13:59 | Update | 36
28 | User <username> | 2009-12-21 13:21 | Install | 1
27 | System <unset> | 2009-12-18 14:59 | Update | 56
26 | User <username> | 2009-12-18 08:46 | Install | 1
history list
Listing Arora browser operations
[root ~]> yum history list arora
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
ID | Login user | Date and time | Action(s) | Altered
————————————————————–
2 | User <username> | 2010-01-19 15:10 | Erase | 1
history list
Yum history info
Show full information by history ID.
Remove Arora browser
[root ~]> yum remove arora
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
Setting up Remove Process
[…]
=====================================================
Package Arch Version Repository Size
=====================================================
Removing:
arora i686 0.10.2-2.fc12 installed 3.7 M
Transaction Summary
=====================================================
Remove 1 Package(s)
Reinstall 0 Package(s)
Downgrade 0 Package(s)
Is this ok [y/N]: y
[…]
Running Transaction
Erasing : arora-0.10.2-2.fc12.i686 1/1
Removed:
arora.i686 0:0.10.2-2.fc12
Complete!
Yum history list
[root ~]> yum history list
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
ID | Login user | Date and time | Action(s) | Altered
————————————————————–
2 | User <username> | 2010-01-19 15:10 | Erase | 1
1 | User <username> | 2010-01-19 14:55 | Update | 3
history list
Show history info for ID 2
[root ~]> yum history info 2
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
Transaction ID : 2
Begin time : Tue Jan 19 15:10:13 2010
Begin rpmdb : 2431:fe4c2c846fd45c9125fb8ab27542a27b22e0d3df
End time : 15:10:27 2010 (14 seconds)
End rpmdb : 2430:2eeb12b0b0f2ef3fcb31b4447b439e76e92e3866
User : User <username>
Return-Code : Success
Transaction performed with:
Installed rpm-4.7.2-1.fc12.i686
Installed yum-3.2.25-1.fc12.noarch
Installed yum-plugin-fastestmirror-1.1.24-2.fc12.noarch
Packages Altered:
Erase arora-0.10.2-2.fc12.i686
history info
Yum history summary
Shows summary of lates operations.
[root ~]> yum history summary
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
Login user | Time | Action(s) | Altered
————————————————————–
User <username> | Last day | E, U | 4
history summary
Yum history repeat
yum history repeat command repeats old operation by history ID.
[root ~]> yum history repeat 2
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
Loading mirror speeds from cached hostfile
* fedora: mirror.cogentco.com
* livna: rpm.livna.org
[…]
Repeating transaction 2, from Tue Jan 19 15:10:13 2010
Erase arora-0.10.2-2.fc12.i686
No package matched to remove
history repeat
Yum history undo
yum history undo simply undo operations by history ID.
Undo Arora browser erase
[root ~]> yum history undo 2
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
Loading mirror speeds from cached hostfile
[…]
Undoing transaction 2, from Tue Jan 19 15:10:13 2010
Erase arora-0.10.2-2.fc12.i686
Resolving Dependencies
–> Running transaction check
—> Package arora.i686 0:0.10.2-2.fc12 set to be updated
–> Finished Dependency Resolution
Dependencies Resolved
=====================================================
Package Arch Version Repository Size
=====================================================
Installing:
arora i686 0.10.2-2.fc12 updates 1.1 M
Transaction Summary
=====================================================
Install 1 Package(s)
Upgrade 0 Package(s)
Total download size: 1.1 M
Is this ok [y/N]: y
Downloading Packages:
arora-0.10.2-2.fc12.i686.rpm | 1.1 MB 00:00
[…]
Running Transaction
Installing : arora-0.10.2-2.fc12.i686 1/1
Installed:
arora.i686 0:0.10.2-2.fc12
Complete!
History list after undo
[root ~]> yum history list arora
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
ID | Login user | Date and time | Action(s) | Altered
————————————————————–
3 | User <username> | 2010-01-19 15:35 | Install | 1
2 | User <username> | 2010-01-19 15:10 | Erase | 1
history list
Yum history redo
yum history redo simply redos operation from yum history by ID.
[root ~]> yum history redo 2
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
[…]
Repeating transaction 2, from Tue Jan 19 15:10:13 2010
Erase arora-0.10.2-2.fc12.i686
Resolving Dependencies
–> Running transaction check
—> Package arora.i686 0:0.10.2-2.fc12 set to be erased
–> Finished Dependency Resolution
Dependencies Resolved
=====================================================
Package Arch Version Repository Size
=====================================================
Removing:
arora i686 0.10.2-2.fc12 installed 3.7 M
Transaction Summary
=====================================================
Remove 1 Package(s)
Reinstall 0 Package(s)
Downgrade 0 Package(s)
Is this ok [y/N]: y
[…]
Running Transaction
Erasing : arora-0.10.2-2.fc12.i686 1/1
Removed:
arora.i686 0:0.10.2-2.fc12
Complete!
Yum history new
yum history new command delete/clear old history listing.
[root ~]> yum history new
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
history new
[root ~]> yum history
Loaded plugins: dellsysidplugin2, fastestmirror, refresh-packagekit
ID | Login user | Date and time | Action(s) | Altered
————————————————————–
history list
by Anil Jalela | Oct 2, 2022 | Linux
Create a CSR certificate for your domain name with help with OpenSSL.
[root@server2 ~]# mkdir /etc/httpd/conf/ssl/csr/www.nitwings.com/ -p
You have new mail in /var/spool/mail/root
[root@server2 ~]# /usr/bin/openssl genrsa 2048 > /etc/httpd/conf/ssl/csr/www.nitwings.com/www.nitwings.com.key
Generating RSA private key, 2048 bit long modulus
……………………………………………………………………+++
…………………+++
e is 65537 (0x10001)
[root@server2 ~]# chmod go-rwx /etc/httpd/conf/ssl/csr/www.nitwings.com/www.nitwings.com.key
[root@server2 ~]# openssl req -new -key /etc/httpd/conf/ssl/csr/www.nitwings.com/www.nitwings.com.key > /etc/httpd/conf/ssl/csr/www.nitwings.com/www.nitwings.com.csr
You are about to be asked to enter information that will be incorporated into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
—–
Country Name (2 letter code) [XX]:IN
State or Province Name (full name) []:Maharashtra
Locality Name (eg, city) [Default City]:Mumbai
Organization Name (eg, company) [Default Company Ltd]:Nitwings Pvt.Ltd
Organizational Unit Name (eg, section) []:SDU
Common Name (eg, your name or your server’s hostname) []:www.nitwings.com
Email Address []:[email protected]
Please enter the following ‘extra’ attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
You have mail in /var/spool/mail/root
[root@server2 ~]#cat /etc/httpd/conf/ssl/csr/www.nitwings.com/www.nitwings.com.csr
submit CSR to SSL provider.
by Anil Jalela | Sep 29, 2022 | Linux
SFC is a Generic shell script compiler. We can use SFC binary to encrypt the shell script. Using SFC you can set the expiry date of your shell script.
yum install shc
shc [ -e date ] [ -m addr ] [ -i iopt ] [ -x cmnd ] [ -l lopt ] [ -o outfile ] [ -ABCDhUHvSr ] -f script
encrypt the blackpost.sh
shc -f blackpost.sh
blackpost.sh is the original unencrypted shell script
blackpost.sh.x is the encrypted shell script in binary format
blackpost.sh.x.c is the C source code of the blackpost.sh file.
This C source code is compiled to create the above encrypted blackpost.sh.x file.
The whole logic behind the shc is to convert the blackpost.sh shell script to blackpost.sh.x.c C program (and of course compile that to generate the blackpost.sh.x executable
Expiration Date for Shell Script:-
shc -e 11/11/2022 -m “call to aniljalela” -f blackpost.sh
Redistributable Encrypted Shell Scripts:-
-r will relax security to create a redistributable binary that executes on other systems that runs the same operating system as the one on which it was compiled.
-v is for verbose
shc -v -r -f blackpost.sh
by Anil Jalela | Sep 29, 2022 | Linux
There are many use cases of proxy servers. It can range from individual Internet access to restricting organizational systems/servers from accessing the outside world or limiting external Internet access to a set of servers on the cloud.
The best way to configure a proxy server is by using Squid Proxy. It is a widely used proxy server.
The concept of a proxy server offers a surprisingly large number of benefits:
Control Internet access in corporate networks
Bandwidth savings for large networks
Improved speed
Privacy
Security
Bypass censorship
yum -y install squid
htpasswd -bc /etc/squid/squid_passwd squidadmin your-password
cp /etc/squid/squid.conf /etc/squid/org_squid.conf
echo ”
auth_param basic program /usr/lib64/squid/basic_ncsa_auth /etc/squid/squid_passwd
acl ncsa_users proxy_auth REQUIRED
http_access allow ncsa_users
acl manager proto cache_object
acl localhost src 127.0.0.1/32
acl to_localhost dst 127.0.0.0/8 0.0.0.0/32
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
http_access allow manager localhost
http_access deny manager
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access deny all
http_port 3128
hierarchy_stoplist cgi-bin ?
coredump_dir /var/spool/squid
cache deny all
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
icp_port 3130
forwarded_for off
request_header_access Allow allow all
request_header_access Authorization allow all
request_header_access Proxy-Authorization allow all
request_header_access Proxy-Authenticate allow all
request_header_access Cache-Control allow all
request_header_access Content-Encoding allow all
request_header_access Content-Length allow all
request_header_access Content-Type allow all
request_header_access Date allow all
request_header_access Expires allow all
request_header_access Host allow all
request_header_access If-Modified-Since allow all
request_header_access Last-Modified allow all
request_header_access Location allow all
request_header_access Pragma allow all
request_header_access Accept allow all
request_header_access Accept-Charset allow all
request_header_access Accept-Encoding allow all
request_header_access Accept-Language allow all
request_header_access Content-Language allow all
request_header_access Mime-Version allow all
request_header_access Retry-After allow all
request_header_access Title allow all
request_header_access Connection allow all
request_header_access Proxy-Connection allow all
request_header_access User-Agent allow all
request_header_access Cookie allow all
request_header_access All deny all
visible_hostname nitwings.com
” > squid.conf
sudo systemctl start squid
sudo systemctl enable squid


